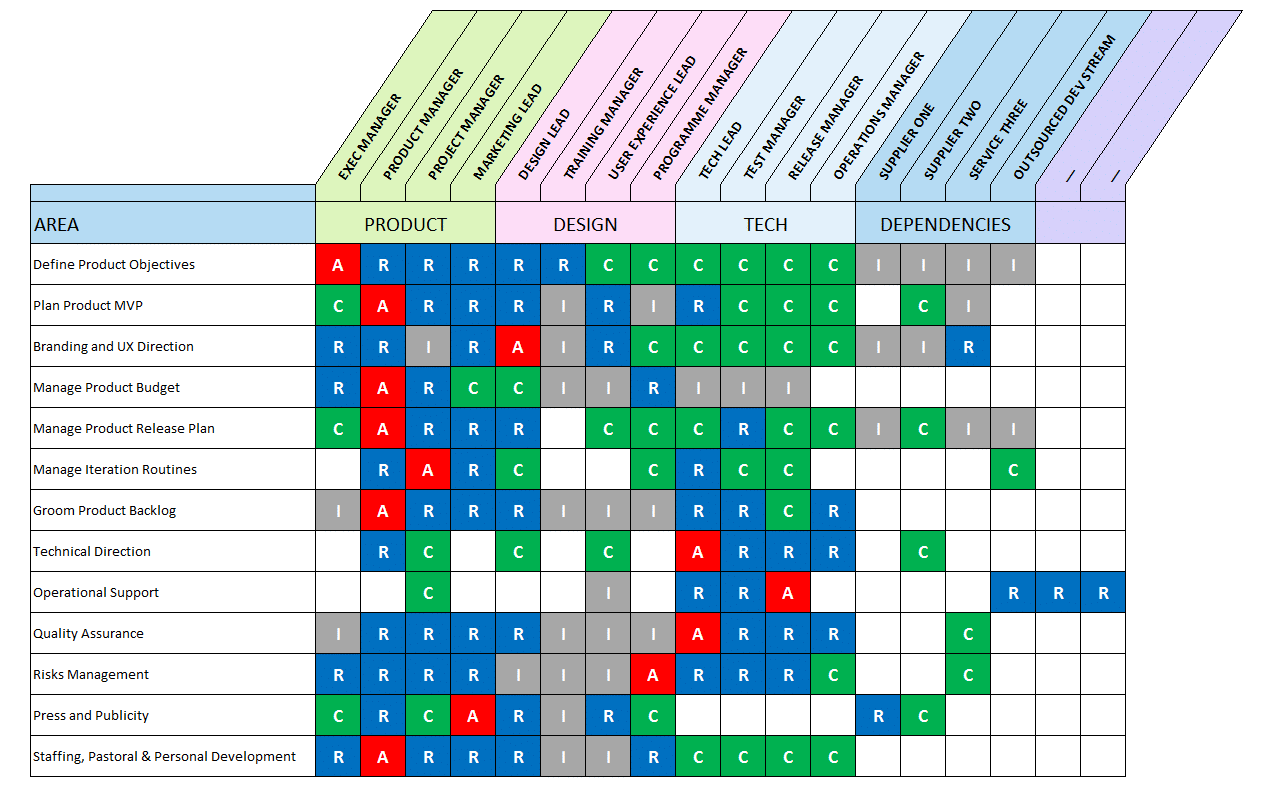
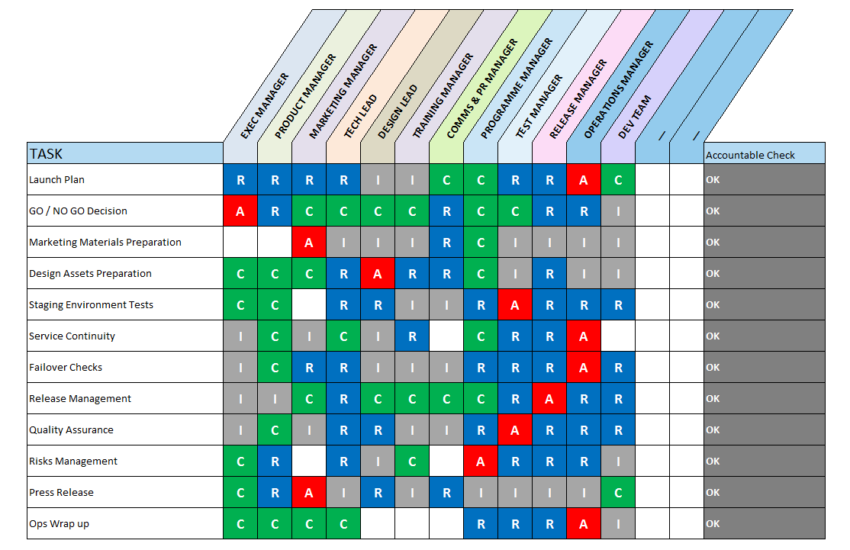
Role-Based Access Control Matrix Template Excel
Role-Based Access Control Matrix Template Excel - This is the first step in role creation. Nist rbac activities nist rbac model (ferraiolo, cugini, kuhn) nist rbac model implementation for the www (rbac/web) administrative tools: Access control and security managers can use this fully editable deck to discuss how the users are grouped into roles based on needs and responsibilities to plan the. Web rbac definition rbac is the idea of assigning system access to users based on their role within an organization. The system needs of a given workforce are analyzed, with users grouped into.
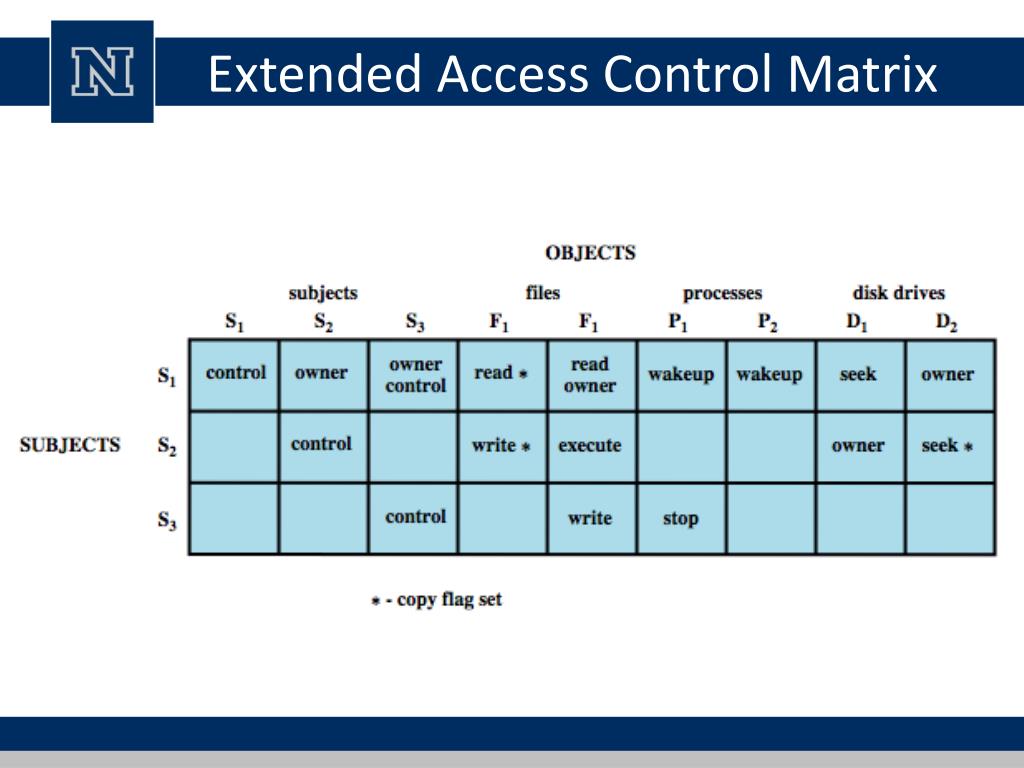
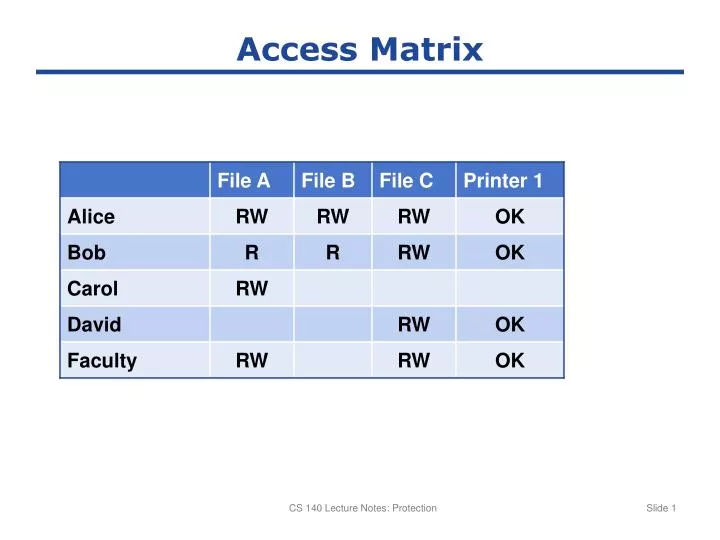
This is the first step in role creation. Other none more business pest ansoff value chain Web view access control as a matrix. Web the rbac permissions matrix displays the type of product roles that are available within each cloud product. | find, read and cite all the research you need on. While the matrix is rarely implemented, access control in real systems is usually based on access control mechanisms, such. Web pdf | the access matrix is a useful model for understanding the behaviour and properties of access control systems.
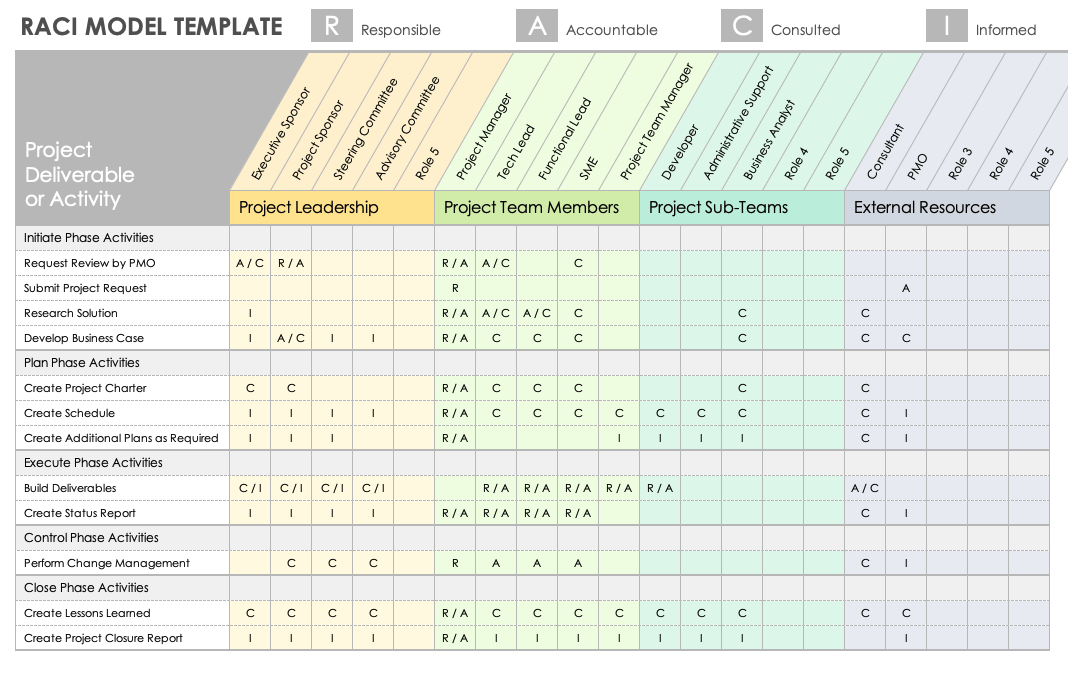
RACI Matrix Template with 3 Formats Excel. Google Sheets Compatible
While the matrix is rarely. Web the role based access control matrix template from clickup provides you with an easy way to ensure appropriate access and keep your organization safe. The system needs of a.
Rbac Excel Template
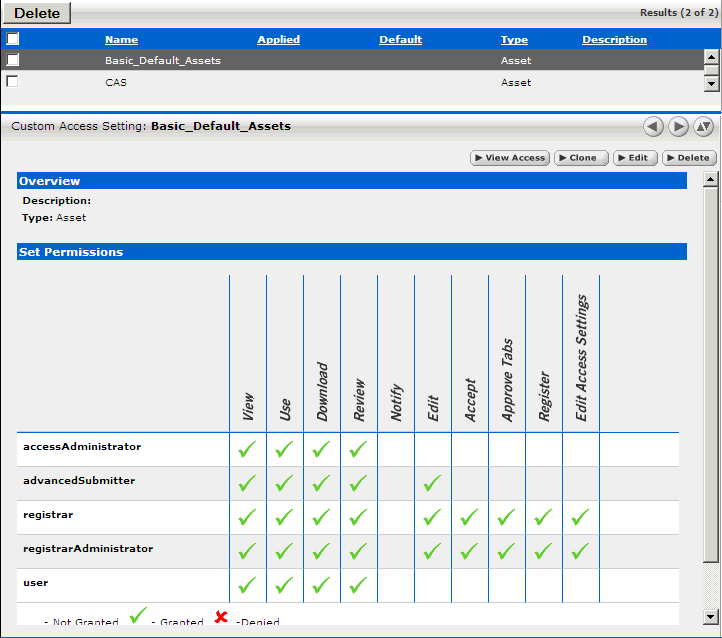
You can export it in multiple formats like jpeg, png and svg and easily add it to word documents, powerpoint (ppt) presentations, excel or any other documents. Each role has a set of permissions that.
Security Matrix in CRM Information Dynamics
For instance, under rbac, a company’s accountant. To get a definition of each of these access levels, see the access level definitions. While the matrix is rarely implemented, access control in real systems is usually.
Application access control matrix template
While the matrix is rarely implemented, access control in real systems is usually based on access control mechanisms, such. In this quickstart, you create a resource group and grant a user access to create and.
Rbac Excel Template
The document is used to assign roles and permissions to users, define the access level of each role, and restrict access to sensitive information or resources. For instance, under rbac, a company’s accountant. Use this.
Excel RACI Matrix Template with 3 Formats
It is used by the majority of medium to large enterprises, and can implement mandatory access control (mac) and discretionary access control (dac). For instance, under rbac, a company’s accountant. Smoothly delegate user access rights.
PPT Lecture 7 Access Control PowerPoint Presentation, free download
This is the first step in role creation. | find, read and cite all the research you need on. The system needs of a given workforce are analyzed, with users grouped into. Should be reasonably.
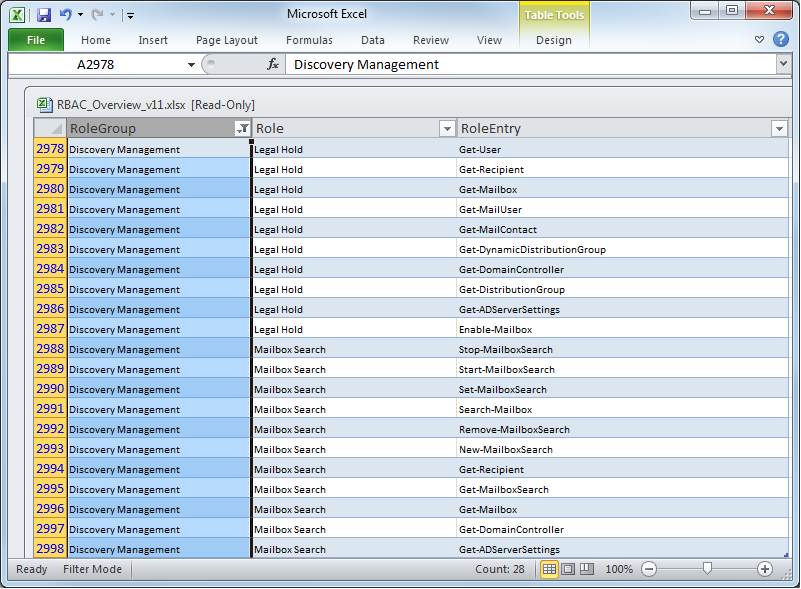
Simplifying RBAC management in Exchange Server 2010
You can assign roles with various levels of permission within your organization. | find, read and cite all the research you need on. Web rbac definition rbac is the idea of assigning system access to.
Free Microsoft Excel RACI Templates Smartsheet
It is used by the majority of medium to large enterprises, and can implement mandatory access control (mac) and discretionary access control (dac). Web rbac definition rbac is the idea of assigning system access to.
PPT Access Matrix PowerPoint Presentation, free download ID4662709
The document is used to assign roles and permissions to users, define the access level of each role, and restrict access to sensitive information or resources. Web view access control as a matrix. Use this.
Role-Based Access Control Matrix Template Excel In this quickstart, you create a resource group and grant a user access to create and manage virtual machines in the resource group. You can control and monitor user activities. Smoothly delegate user access rights to files, drives. Web role based access control (rbac) (also called role based security), as formalized in 1992 by david ferraiolo and rick kuhn, has become the predominant model for advanced access control because it reduces this cost. | find, read and cite all the research you need on.