Intro
Discover 5 ways to deidentify data, ensuring secure anonymization and protection of sensitive information through data masking, encryption, and more, for compliance and risk reduction in data privacy and security.
Data deidentification is a crucial process in ensuring the privacy and security of sensitive information. With the increasing amount of data being collected and stored, it's essential to protect individuals' identities and prevent unauthorized access. Deidentification is the process of removing or modifying personal identifiable information (PII) from a dataset to prevent identification of individuals. In this article, we will explore five ways to deidentify data, their benefits, and best practices.
Deidentification is essential in various industries, including healthcare, finance, and education, where sensitive information is collected and stored. The process helps to prevent data breaches, protect individuals' privacy, and comply with regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Deidentification can be applied to various types of data, including structured and unstructured data, and can be performed using various techniques and tools.
The importance of deidentification cannot be overstated. With the increasing number of data breaches and cyberattacks, it's essential to take proactive measures to protect sensitive information. Deidentification helps to reduce the risk of data breaches, prevent identity theft, and protect individuals' privacy. Moreover, deidentification enables organizations to share data while maintaining confidentiality, which is essential for research, analysis, and business purposes.
What is Data Deidentification?
Benefits of Data Deidentification
5 Ways to Deidentify Data

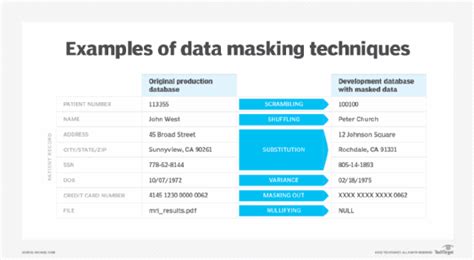
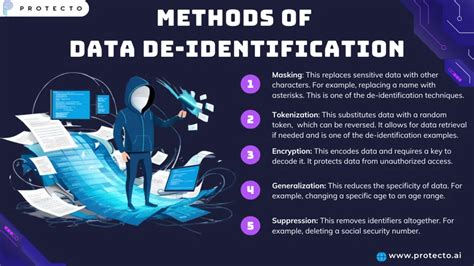
1. Data Masking
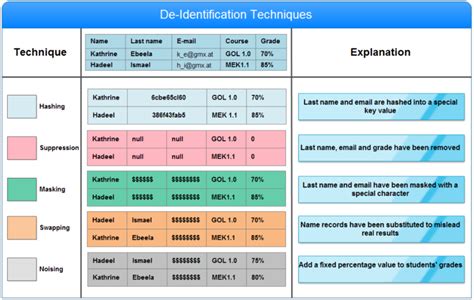
Data masking is a technique that involves replacing sensitive information with fictional data. For example, replacing names with fictional names or replacing addresses with fictional addresses. Data masking is a simple and effective way to deidentify data, but it may not be suitable for all types of data.
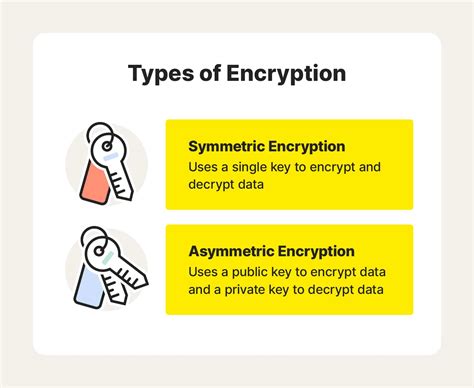
2. Data Encryption
Data encryption is a technique that involves converting sensitive information into an unreadable format. For example, encrypting names, addresses, and social security numbers. Data encryption is a secure way to deidentify data, but it may require specialized software and expertise.
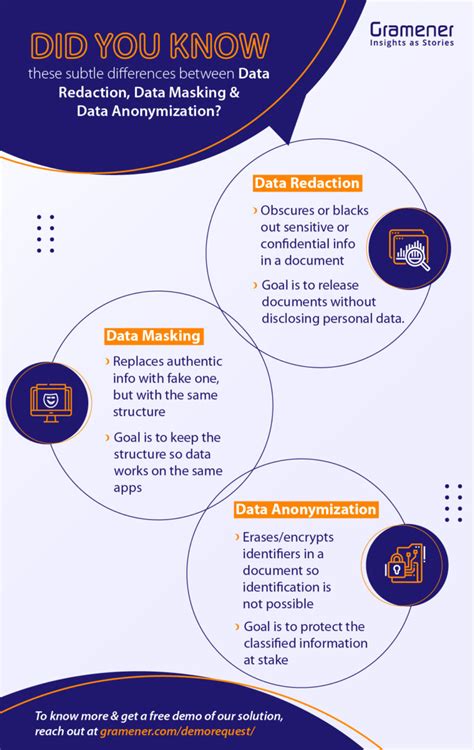
3. Data Anonymization
Data anonymization is a technique that involves removing direct and indirect identifiers from a dataset. For example, removing names, addresses, and dates of birth. Data anonymization is a effective way to deidentify data, but it may not be suitable for all types of data.
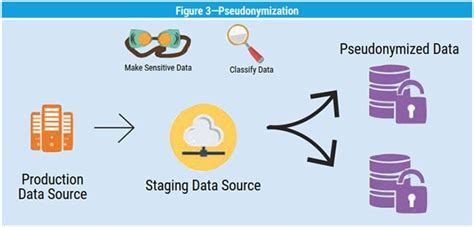
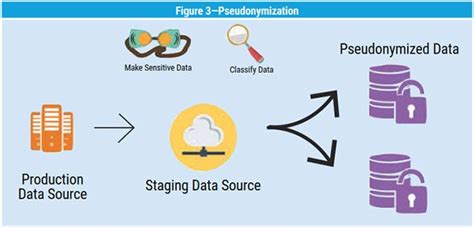
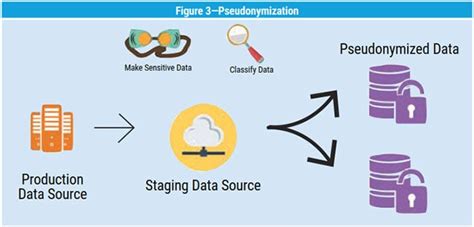
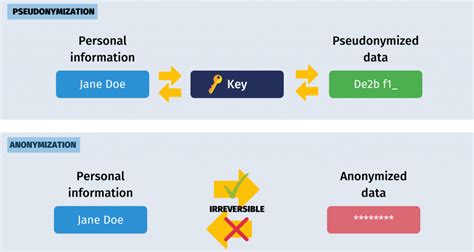
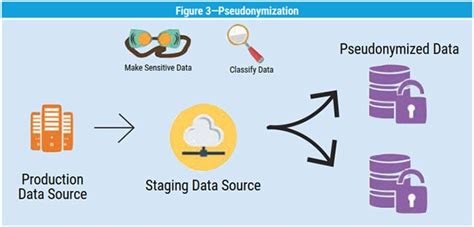
4. Data Pseudonymization
Data pseudonymization is a technique that involves replacing direct identifiers with fictional identifiers. For example, replacing names with fictional names or replacing social security numbers with fictional numbers. Data pseudonymization is a simple and effective way to deidentify data, but it may not be suitable for all types of data.
5. Data Aggregation
Data aggregation is a technique that involves combining data from multiple sources to create a new dataset. For example, combining data from multiple hospitals to create a new dataset. Data aggregation is a effective way to deidentify data, but it may require specialized software and expertise.
Best Practices for Data Deidentification
- Using a combination of deidentification techniques to ensure maximum protection
- Using specialized software and expertise to deidentify data
- Testing deidentified data to ensure that it is secure and useful
- Documenting deidentification processes and procedures
- Training personnel on deidentification techniques and best practices
Challenges of Data Deidentification
- Ensuring that deidentified data is secure and useful
- Balancing the need for data protection with the need for data sharing and analysis
- Complying with regulations such as GDPR and HIPAA
- Managing the complexity of deidentification processes and procedures
- Ensuring that personnel are trained and aware of deidentification techniques and best practices
Gallery of Data Deidentification Techniques
Data Deidentification Techniques Image Gallery


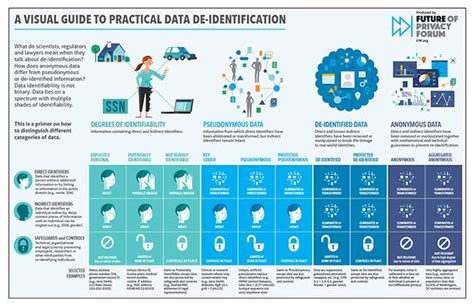
What is data deidentification?
+Data deidentification is the process of removing or modifying personal identifiable information (PII) from a dataset to prevent identification of individuals.
Why is data deidentification important?
+Data deidentification is important because it helps to protect sensitive information, prevent data breaches, and comply with regulations such as GDPR and HIPAA.
What are the benefits of data deidentification?
+The benefits of data deidentification include protecting sensitive information, preventing data breaches, complying with regulations, and enabling data sharing and analysis.
What are the challenges of data deidentification?
+The challenges of data deidentification include ensuring that deidentified data is secure and useful, balancing the need for data protection with the need for data sharing and analysis, and complying with regulations.
What are the best practices for data deidentification?
+The best practices for data deidentification include using a combination of deidentification techniques, using specialized software and expertise, testing deidentified data, documenting deidentification processes and procedures, and training personnel on deidentification techniques and best practices.
In conclusion, data deidentification is a crucial process in ensuring the privacy and security of sensitive information. By using a combination of deidentification techniques, such as data masking, data encryption, data anonymization, data pseudonymization, and data aggregation, organizations can protect sensitive information, prevent data breaches, and comply with regulations. It's essential to follow best practices for data deidentification, including using specialized software and expertise, testing deidentified data, documenting deidentification processes and procedures, and training personnel on deidentification techniques and best practices. We invite you to share your thoughts and experiences on data deidentification, and to ask any questions you may have on this topic.