Intro
The importance of spreadsheet security cannot be overstated, particularly when it comes to Excel, one of the most widely used spreadsheet programs in the world. Excel's versatility and power make it an indispensable tool for businesses, organizations, and individuals alike, but this widespread use also means that it can be a vulnerable target for security threats. As we delve into the world of Excel potential security concerns, it's essential to understand the risks associated with using this software and the steps that can be taken to mitigate them.
Excel's potential security concerns are multifaceted and can have severe consequences if left unaddressed. From malicious macros and add-ins to data breaches and phishing attacks, the threats are numerous and constantly evolving. Moreover, the sheer volume of data that is stored and processed in Excel spreadsheets makes them a lucrative target for cybercriminals. As such, it's crucial for users to be aware of the potential security risks and take proactive measures to protect themselves and their organizations.
The widespread use of Excel has also led to the development of various security threats that are specifically designed to target this software. For instance, malicious macros can be used to spread viruses, Trojan horses, and other types of malware, while add-ins can be used to steal sensitive data or compromise system security. Furthermore, the use of weak passwords or inadequate access controls can provide an entry point for unauthorized users, who can then exploit vulnerabilities in the software to gain access to sensitive data.
Understanding Excel Security Risks
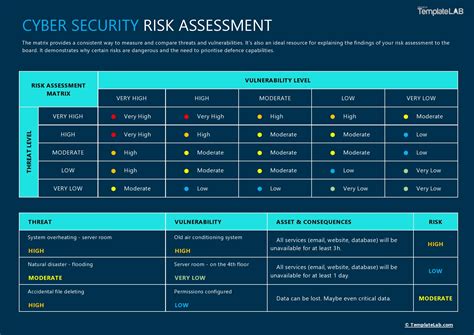
To effectively address Excel potential security concerns, it's essential to understand the various types of risks that are associated with this software. These risks can be broadly categorized into several key areas, including data security, macro security, add-in security, and user security. By understanding these risks and taking proactive measures to mitigate them, users can significantly reduce the likelihood of a security breach and protect their sensitive data.
Types of Excel Security Risks
Some of the most common types of Excel security risks include: * Data breaches: These occur when sensitive data is accessed or stolen by unauthorized users. * Macro viruses: These are viruses that are embedded in Excel macros and can spread to other computers when the macro is executed. * Add-in vulnerabilities: These occur when add-ins are used to steal sensitive data or compromise system security. * Phishing attacks: These are attacks that are designed to trick users into revealing sensitive information, such as passwords or credit card numbers. * Weak passwords: These are passwords that are easily guessable or can be cracked using brute force methods.Protecting Against Excel Security Risks
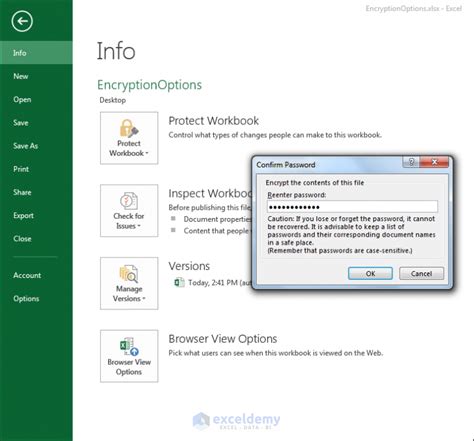
Protecting against Excel security risks requires a combination of technical, administrative, and user-based controls. Some of the key measures that can be taken to protect against these risks include:
- Implementing strong access controls, such as passwords and multi-factor authentication.
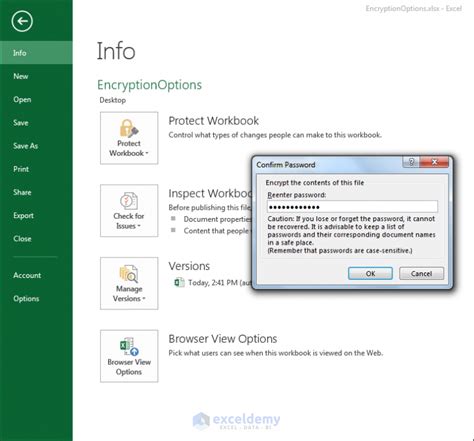
- Using encryption to protect sensitive data.
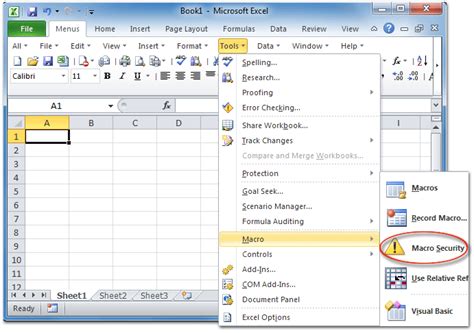
- Disabling macros and add-ins that are not necessary.
- Implementing regular software updates and patches.
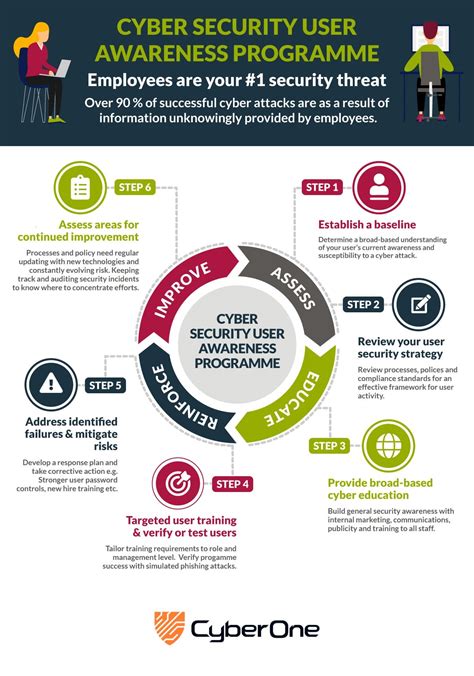
- Providing user training and awareness programs to educate users about the risks associated with Excel and the steps that can be taken to mitigate them.
Best Practices for Excel Security
Some best practices for Excel security include: * Using strong, unique passwords for all Excel files and worksheets. * Enabling macro security and disabling macros that are not necessary. * Using encryption to protect sensitive data. * Implementing regular backups and version control. * Providing user training and awareness programs to educate users about the risks associated with Excel and the steps that can be taken to mitigate them.Excel Security Tools and Features
Excel provides a range of security tools and features that can be used to protect against security risks. Some of the key tools and features include:
- Macro security: This feature allows users to control which macros are enabled and which are disabled.
- Encryption: This feature allows users to protect sensitive data by encrypting it.
- Access controls: This feature allows users to control who can access and modify Excel files and worksheets.
- Auditing: This feature allows users to track changes made to Excel files and worksheets.
- Digital signatures: This feature allows users to verify the authenticity and integrity of Excel files and worksheets.
Using Excel Security Tools and Features
To use Excel security tools and features effectively, users should: * Enable macro security and disable macros that are not necessary. * Use encryption to protect sensitive data. * Implement access controls, such as passwords and multi-factor authentication. * Use auditing to track changes made to Excel files and worksheets. * Use digital signatures to verify the authenticity and integrity of Excel files and worksheets.Excel Security Risks and Mitigations

Excel security risks can be mitigated by implementing a range of technical, administrative, and user-based controls. Some of the key risks and mitigations include:
- Data breaches: Implementing access controls, such as passwords and multi-factor authentication, and using encryption to protect sensitive data.
- Macro viruses: Disabling macros and add-ins that are not necessary and implementing regular software updates and patches.
- Add-in vulnerabilities: Disabling add-ins that are not necessary and implementing regular software updates and patches.
- Phishing attacks: Providing user training and awareness programs to educate users about the risks associated with phishing attacks and the steps that can be taken to mitigate them.
- Weak passwords: Implementing strong, unique passwords for all Excel files and worksheets.
Excel Security Risks and Mitigations Best Practices
Some best practices for Excel security risks and mitigations include: * Implementing a range of technical, administrative, and user-based controls to protect against security risks. * Providing user training and awareness programs to educate users about the risks associated with Excel and the steps that can be taken to mitigate them. * Implementing regular software updates and patches to ensure that Excel is up-to-date and secure. * Using encryption to protect sensitive data. * Implementing access controls, such as passwords and multi-factor authentication, to control who can access and modify Excel files and worksheets.Excel Security Gallery




What are the most common Excel security risks?
+The most common Excel security risks include data breaches, macro viruses, add-in vulnerabilities, phishing attacks, and weak passwords.
How can I protect against Excel security risks?
+To protect against Excel security risks, you can implement a range of technical, administrative, and user-based controls, such as enabling macro security, using encryption, and providing user training and awareness programs.
What are some best practices for Excel security?
+Some best practices for Excel security include implementing strong access controls, using encryption to protect sensitive data, and providing user training and awareness programs to educate users about the risks associated with Excel and the steps that can be taken to mitigate them.
In conclusion, Excel potential security concerns are a pressing issue that requires attention and action from users, organizations, and Microsoft. By understanding the various types of security risks associated with Excel and taking proactive measures to mitigate them, users can significantly reduce the likelihood of a security breach and protect their sensitive data. As the use of Excel continues to evolve, it's essential to stay ahead of the curve and implement the latest security tools and features to ensure the integrity and confidentiality of sensitive data. We invite you to share your thoughts and experiences with Excel security in the comments below, and to explore our other articles and resources on this topic.